![\begin{program*}
\> \\
\> switch\_inv(E; tr) ==\\
\> \mforall{}i,j,k:\mBbbN{}\...
...eg{}\muparrow{}(is-send$_{\mbox{\small {E}}}$\ \\
\> tr[k'])))))
\end{program*}](img69.png)
![\begin{program*}
\> \\
\> i switchR$_{\mbox{\small {tr}}}$\ j ==\\
\> (\muparr...
...((j < i)\\
\> \mwedge{} tr[i] somewhere delivered before tr[j]))
\end{program*}](img71.png)
![\begin{program*}
\> \\
\> \mforall{}E:TaggedEventStruct. \mforall{}tr:\vert E\v...
...}}}$\ tr[i])\\
\> = (tag$_{\mbox{\small {E}}}$\ \\
\> tr[j]))))
\end{program*}](img73.png)
We want to show that a strengthening of switch_inv
![]() refines switch-decomposable
refines switch-decomposable
![]() .
For a non null trace tr satisfying switch_inv
.
For a non null trace tr satisfying switch_inv
![]() tr we must find the criterion
Q on the times ||tr|| that satisfies the five properties in the definition
of switch-decomposability. If tr also satisfies Causal
tr we must find the criterion
Q on the times ||tr|| that satisfies the five properties in the definition
of switch-decomposability. If tr also satisfies Causal
![]() tr then it must contain
a send event and hence there must be a time ls which is the time of the last send
event in tr. We will define Q to hold on all times related to ls by switchR
tr then it must contain
a send event and hence there must be a time ls which is the time of the last send
event in tr. We will define Q to hold on all times related to ls by switchR
![]() .
.
![]()
It is fairly easy to show that Q has the first four of the five required properties.
First, Q is decidable because switchR
![]() is decidable and the transitive closure
of a decidable relation over a finite domain is also decidable.
Second, Q is non empty beacause Q ls holds.
The third requirement follows from the the fact that ls is the time of a send event
and the following lemma, which is proved by induction
on the transitive closure from the fact that switchR
is decidable and the transitive closure
of a decidable relation over a finite domain is also decidable.
Second, Q is non empty beacause Q ls holds.
The third requirement follows from the the fact that ls is the time of a send event
and the following lemma, which is proved by induction
on the transitive closure from the fact that switchR
![]() relates only times of
send events.
relates only times of
send events.
![]()
![\begin{program*}
\> \\
\> \mforall{}E:EventStruct. \mforall{}tr:\vert E\vert Li...
...row{} (\muparrow{}(is-send$_{\mbox{\small {E}}}$\ \\
\> tr[i])))
\end{program*}](img76.png)
Similarly, the fourth requirement, that the events of times satisfying Q all have the
same tag, is a consequence of the following lemma,
proved by induction from lemma 5.3.1.
![]()
![\begin{program*}
\> \\
\> \mforall{}E:TaggedEventStruct. \mforall{}tr:\vert E\v...
...}}$\ tr[i])\\
\> = (tag$_{\mbox{\small {E}}}$\ \\
\> tr[j])))))
\end{program*}](img78.png)
It remains only to establish the fifth property of Q, namely,
![]()
To prove this property of Q we will need a stronger invariant than the property
switch_inv
![]() Causal
Causal
![]() used so far. Without strengthening the invariant
we can prove a weaker version of the requirement. We can prove
used so far. Without strengthening the invariant
we can prove a weaker version of the requirement. We can prove
![]()
This establishes the requirement for the case when the event at time j
is a send event, and we need this lemma to prove the full requirement.
For this lemma, the only assumption we need is that ls is the time of the
last send event.
![]()
proof:
We assume that ls is the time of the last send, that i j, that (is-send
![]() tr[j]), and that
i (switchR
tr[j]), and that
i (switchR
![]() ) ls. So, for some n, i switchR
) ls. So, for some n, i switchR
![]()
![]() ls,
and we prove by induction on n that j (switchR
ls,
and we prove by induction on n that j (switchR
![]() ) ls.
When n = 0, then i = ls, so ls j. Since ls is the last send,
we have j = ls and hence, j (switchR
) ls.
When n = 0, then i = ls, so ls j. Since ls is the last send,
we have j = ls and hence, j (switchR
![]() ) ls.
Now 0 < n, and i switchR
) ls.
Now 0 < n, and i switchR
![]()
![]() ls, so by definition,
there is a time z such that
ls, so by definition,
there is a time z such that
i switchR
![]() z and z switchR
z and z switchR
![]()
![]() ls.
If z j, then by induction, j (switchR
ls.
If z j, then by induction, j (switchR
![]() ) ls. So, we may assume j < z.
Also, if j = i, then we have j (switchR
) ls. So, we may assume j < z.
Also, if j = i, then we have j (switchR
![]() ) ls, by hypothesis.
So, we may assume i < j. So we also have i < z, and since i switchR
) ls, by hypothesis.
So, we may assume i < j. So we also have i < z, and since i switchR
![]() z, we
must have tr[z] somewhere delivered before tr[i].
Then by lemma 4.3.1, we have
tr[z] somewhere delivered before tr[j] tr[j] somewhere delivered before tr[i].
In the first case, because j < z we have j switchR
z, we
must have tr[z] somewhere delivered before tr[i].
Then by lemma 4.3.1, we have
tr[z] somewhere delivered before tr[j] tr[j] somewhere delivered before tr[i].
In the first case, because j < z we have j switchR
![]() z and hence j switchR
z and hence j switchR
![]()
![]() ls.
In the second case, because i < j we have j switchR
ls.
In the second case, because i < j we have j switchR
![]() i
and hence j switchR
i
and hence j switchR
![]()
![]() ls. So, in either case, j (switchR
ls. So, in either case, j (switchR
![]() ) ls and we are done.
) ls and we are done.
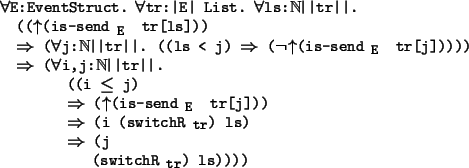
To prove the complete closure requirement, i,j:||tr||. ((Q i) (i j) (C(Q) j)),
we will have to assume that the trace tr has a certain normal form.
We will be able to put a trace into normal form using only operations that preserve
the relation asyncR
![]() delayableR
delayableR
![]() . So, for asynchronous, delayable properties,
P, if P holds of the normal form of trace tr, then it also holds of tr.
. So, for asynchronous, delayable properties,
P, if P holds of the normal form of trace tr, then it also holds of tr.
We put a trace into normal form by moving send events as late as possible and by reordering asynchronous deliver events to match the order of their send events. More constructively, we apply the following normalization algorithm. If we find an adjacent pair of events (a,b) in the trace where a is a send event and b is a deliver event, then, unless they contain the same message, we swap the two events so that the send event a occurs later than the deliver event b. If we find an adjacent pair of deliver events (a,b) for which there are corresponding send events that occur in the opposite order, then if events a and b are at different locations, we swap them so that their order is the same as their corresponding send events. Under some additional assumptions, we will prove that this algorithm terminates and results in a trace that satisfies the following normal form property, that we call asynchronous-delayable normal form or AD-normal.
![\begin{program*}
\> \\
\> AD-normal$_{\mbox{\small {E}}}$\ tr ==\\
\> \mforall...
...])\\
\> = (loc$_{\mbox{\small {E}}}$\ \\
\> tr[i\\
\> + 1]))))
\end{program*}](img87.png)
Assuming that trace tr satisfies AD-normal
![]() and two additional properties,
No-dup-deliver
and two additional properties,
No-dup-deliver
![]() and Causal
and Causal
![]() , and the assumptions
needed for lemma 5.3.4, we can now prove
, and the assumptions
needed for lemma 5.3.4, we can now prove
![]()
proof: We proceed by induction on j - i.
If (j - i) = 0, then j = i, so Q j, and hence C(Q) j.
If (j - i) > 0, then i (j - 1).
We assume Q i, and this implies that tr[i] is a send event.
We must show C(Q) j.
If the event at time j is a send event, then lemma 5.3.4
implies that Q j.
So we may assume that tr[j] is a deliver event.
case 1 tr[j - 1] is a send event. Lemma 5.3.4 implies that
Q (j - 1) and the
normal form implies that (tr[j - 1] =msg=
![]() tr[j]). Hence C(Q) j.
case 2 tr[j - 1] is a deliver event. By induction, we have C(Q) (j - 1), so
there is a time k such that Q k and the events at times k and j - 1 have the
same message. So the event at time k is the send event for the deliver event at time
j - 1. By the Causal
tr[j]). Hence C(Q) j.
case 2 tr[j - 1] is a deliver event. By induction, we have C(Q) (j - 1), so
there is a time k such that Q k and the events at times k and j - 1 have the
same message. So the event at time k is the send event for the deliver event at time
j - 1. By the Causal
![]() property, there is also a time j' when the send event
for the delivery at time j occured. We claim that Q j' holds,
and hence C(Q) j.
case 2.1 j' < k. In this case, the deliveries at times j - 1 and j are out of
order, so by the normal form property, they must have the same location, call it p.
Since we have the No-dup-deliver
property, there is also a time j' when the send event
for the delivery at time j occured. We claim that Q j' holds,
and hence C(Q) j.
case 2.1 j' < k. In this case, the deliveries at times j - 1 and j are out of
order, so by the normal form property, they must have the same location, call it p.
Since we have the No-dup-deliver
![]() property, there cannot be any delivery of
the message sent at time j' to location p other than the one at time j.
Therefore we have tr[k] somewhere delivered before tr[j'], and this implies that
j' switchR
property, there cannot be any delivery of
the message sent at time j' to location p other than the one at time j.
Therefore we have tr[k] somewhere delivered before tr[j'], and this implies that
j' switchR
![]() k. Since Q k, and since Q is closed under switchR
k. Since Q k, and since Q is closed under switchR
![]() ,
we get Q j'.
case 2.2 k j'. In this case, since the event at time j' is a send and since
Q k, lemma 5.3.4 implies that Q j'.
,
we get Q j'.
case 2.2 k j'. In this case, since the event at time j' is a send and since
Q k, lemma 5.3.4 implies that Q j'.
Putting together everything we have proved in this section, we see that we have
proved the following
![]()
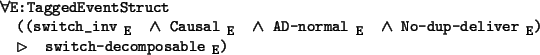
The next theorem combines all the previous lemmas.
![]()
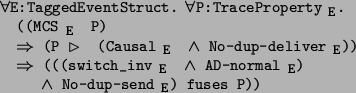
proof: Using lemma 5.0.8, it is enough to show that I fuses P where
![]()
We prove this using MCS-induction. The hypotheses of the MCS-induction require
us to show that I is a safety property
and that I is single-tag-decomposable.
It is straightforward to show that each of
the six conjoined properties in I is a safety property, and therefore I
is a safety property. By theorem 5.2, to show that I
is single-tag decomposable, it is enough
to show that I is switch-decomposable, since I refines Tag-by-msg
![]() ,
Causal
,
Causal
![]() , and No-dup-send
, and No-dup-send
![]() . But I refines
. But I refines
![]()
and, by theorem 5.3
, that property refines the switch-decomposabilty property.